My-Tiny.Net :: Networking with Virtual Machines
Basics of Penetration Testing
Verifying that your firewall rules are performing as intended should be a regular procedure. Once you have identified any unfiltered ports or other issues, you should review your firewall rules to ensure that access to all services is controlled, and that filters and rules are performing as intended. After changes are implemented, run the audit scan again to ensure that your changes achieve the desired effect.
hping is a packet assembler/analyzer used for crafting TCP/IP packets. You can experiment probing and analysing your firewalls and network by sending a variety of probe types with different flag settings. It's possible to use most of the options for the scan mode, so the packets you use to scan can be tuned to uncover different aspects of the firewall layer.
Background:
The TCP segment (packet) header has six flag bits that can be set independently. A mnemonic to remember them in order is 'Unskilled Attackers Pester Real Security Folks'.PSH (PuSH) and URG (URGent) are used to ensure priority over other packets for processing when a packet is received. The CWR and ECN bits may be used together by a client and server that have the ability to use RFC 3168 Explicit Congestion Notification.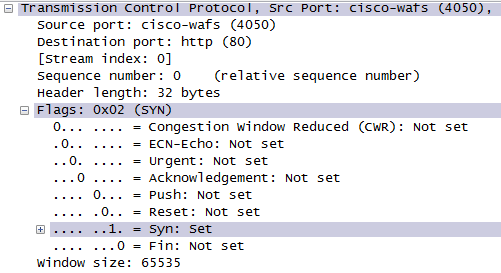
Four flag bits are used to describe the state of the connection:
- SYN (SYNchronise) is used for starting a connection
- ACK (ACKnowledge) is used to confirm packets are received
- FIN (FINish) is used for ending a connection
- RST (ReSeT) is used to denote that no service is listening on the port
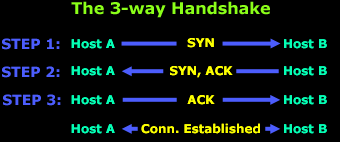
The initial connection with a TCP service is established with the "TCP 3 way handshake". First a SYN is sent to a port that has a service bound to it (an open port). The server side will see the SYN and respond with SYN + ACK, with the client answering the SYN + ACK with an ACK, which completes the connection set up. 
After this, an ACK is sent after receiving each "window size" group of packets (details are beyond our scope, but here is a nice graphic). 
When a host sends a FIN flag to close a connection, it may continue to receive data until the remote host has also closed the connection, although this only occurs under certain circumstances. Full details-:
http://www.firewall.cx/networking-topics/protocols/tcp/136-tcp-flag-options.html
http://www.firewall.cx/networking-topics/protocols/tcp/137-tcp-window-size-checksum.html
Packet Crafting
hping allow you to set any of the flag bits in a TCP, UDP, ICMP or RAW-IP packet to see how the target will react. The default is to send empty (0 data byte) packets, but there are lots of options for tuning the payload. Most scan types send and receive raw packets, and so are only available to privileged users, meaning root access on Unix/Linux or an administrator account on Windows.hping is on all TinyNet machines. Try it out:
hping --scan known 192.168.56.101
- The man page is good:
man 8 hpingor http://www.hping.org/manpage.html
- Sections 5 and 6 of http://www.radarhack.com/tutorial/hping.pdf are particularly interesting, showing how a data payload and signature can be used with the hping listen feature (-9 switch) to transfer files.
Logfiles can grow quickly with pentesting. If you want a clean file to begin with
- stop the syslog daemon with
/etc/rc.d/rc.syslog stop- rename the existing logfile
- create a new one with something like
echo "Test Record" >>log.log(using the proper file name)- restart the syslog daemon with
/etc/rc.d/rc.syslog startMultitail is an ideal tool for watching tests of firewall rules
Check the Penetration Testing (PenTest) section of the Multitail page
under Utilities on the menu.
Null Scan: This scan sets the sequence number to zero and no flags set in the packet. If the port is closed we get a RST packet in reply, and no reply if the port is open.
This is the default behaviour for hping:
hping 192.168.56.101 sends a TCP null-flags packet to port 0 of the target host every second and shows the replies. Port 0 is used by default because it's very strange for it to be in the LISTEN state.
The iptables command to close this off is simple:
iptables -A INPUT -p tcp --tcp-flags ALL NONE -j DROP
SYN Scan: In a TCP connection a packet with just the SYN flag set is used in the connection setup routine, and should get a SYN+ACK in reply if the port is open, and RST+ACK if the port is closed. This will send a single packet with the SYN flag set to port 80 from port 5050:
hping -c 1 -V -p 80 -s 5050 -S 192.168.56.101
ACK Scan: In a TCP connection a packet with just the ACK flag set is used in both the connection setup and connection close routines. A lone ACK packet without the rest of the routine should receive a RST packet in reply if the port is open, and no reply if the port is closed. This will send a single packet with the ACK flag set to port 80 from port 5050:
hping -c 1 -V -p 80 -s 5050 -A 192.168.56.101
Since SYN and ACK packets are part of the normal operation of TCP, there is no iptables command to close this off - we need to rely on an Intrusion Detection System (IDS) to warn about these scans.
FIN Scan: In a TCP connection a FIN+ACK packet is used to start the connection closing routine. With just the FIN flag set, we expect to receive a RST+ACK packet in reply if the port is closed, and no reply if the port is open. This will send a single packet with the FIN flag set to port 80 from port 5050:
hping -c 1 -V -p 80 -s 5050 -F 192.168.56.101
The iptables command to close this off says FIN+ACK is valid, FIN alone is not.
iptables -A INPUT -p tcp --tcp-flags FIN,ACK FIN -j DROP
Xmas Scan: This scan sets the sequence number to zero and set the URG+PSH+FIN flags in the packet (lighting it up like a Christmas tree). If the port is closed we get a RST packet in reply, and no reply if the port is open. This type of packet requires more processing than the usual packets, so it can be used to perform a DOS attack on the server. The hping command is:
hping -c 1 -V -p 80 -s 5050 -M 0 -UPF 192.168.56.101
The iptables command to close this off is
iptables -A INPUT -p tcp --tcp-flags ALL FIN,PSH,URG -j DROP
LAND Attack: LAND stands for Local Area Network Denial. In this attack, a packet is spoofed with source address as the address of the target itself, i.e., the source and destination addresses are the same. The target machine ends up replying to itself continuously. This is a quite famous DOS attack that was quite effective on Windows NT in the old days. The hping command, setting SYN and using a known open port is:
hping -S -a 192.168.56.101 -p 80 192.168.56.101
The iptables command to close this off would be like this
iptables -A INPUT -s 192.168.56.101 -d 192.168.56.101 -j DROP
but it would work better from a script, to handle dynamic addresses
LN=$(ifconfig |grep -v 127.0.0.1 |grep inet |grep -v inet6) IA=$(echo $LN |cut -d " " -f 2 |cut -d ":" -f 2) iptables -A INPUT -s $IA -d $IA -j DROP
SYN flood: The attacker sends a large number of SYN requests with a spoofed source IP address. The target replies with SYN+ACK, and allocates its resources for the connection, but never gets an ACK reply. Eventually the target machine's resources are exhausted and it stops serving legitimate requests.
With hping it is easy to send 1000 packets per second with a random source address to a single port:
hping --faster -S --rand-source -p 80 --keep 192.168.56.101
This attack and some other DOS/DDOS attacks can be controlled by limiting the incoming TCP connection request packets. Note that only new connection requests need to be controlled, and the limit set should be based on the capacity of the server.
iptables -A INPUT -p tcp -m state --state NEW -m limit --limit 2/second --limit-burst 2 -j ACCEPT
iptables -A INPUT -p tcp -m state --state NEW -j DROP
If you want to log the dropped packets, don't forget to apply a limit to the logging as well, or you will just be moving the resource problem from one point to another!
Smurf Attack: Broadcast a large number of ICMP echo requests with source IP address spoofed to that of target's IP address. All the machines on the subnet receive this broadcast message and send an ICMP echo reply to the target.
This command will send 100 "pings" per second:
hping -1 -i u1000 -a 192.168.56.101 192.168.56.255
This attack can be controlled with iptables the same way as the SYN flood:
iptables -A INPUT -p icmp -m limit --limit 2/second --limit-burst 2 -j ACCEPT
iptables -A INPUT -p icmp -j DROP